A series of significant cybersecurity incidents have rocked the IT world recently with major companies, including Google, reporting data breaches due to hacking attacks that included Salesforce connected apps. These incidents have shed harsh light on the vulnerabilities exposed through having loose Salesforce security.
We’ve covered the massive costs of data breaches in prior articles, and while the full impact of recent branches is yet to be fully known, companies are undoubtedly suffering incredible financial losses and damaged credibility.
Without proper defenses in place, malicious third parties can access your sensitive data through Salesforce connected applications, compromising your loyal customers and trusted stakeholders. There are several security measures you can put in place, and our free health check can help kickstart your audit!
Let’s review how these cybersecurity events happened and what steps you can take to ensure your own organization doesn’t get added to the growing list of victims.
What exactly happened?
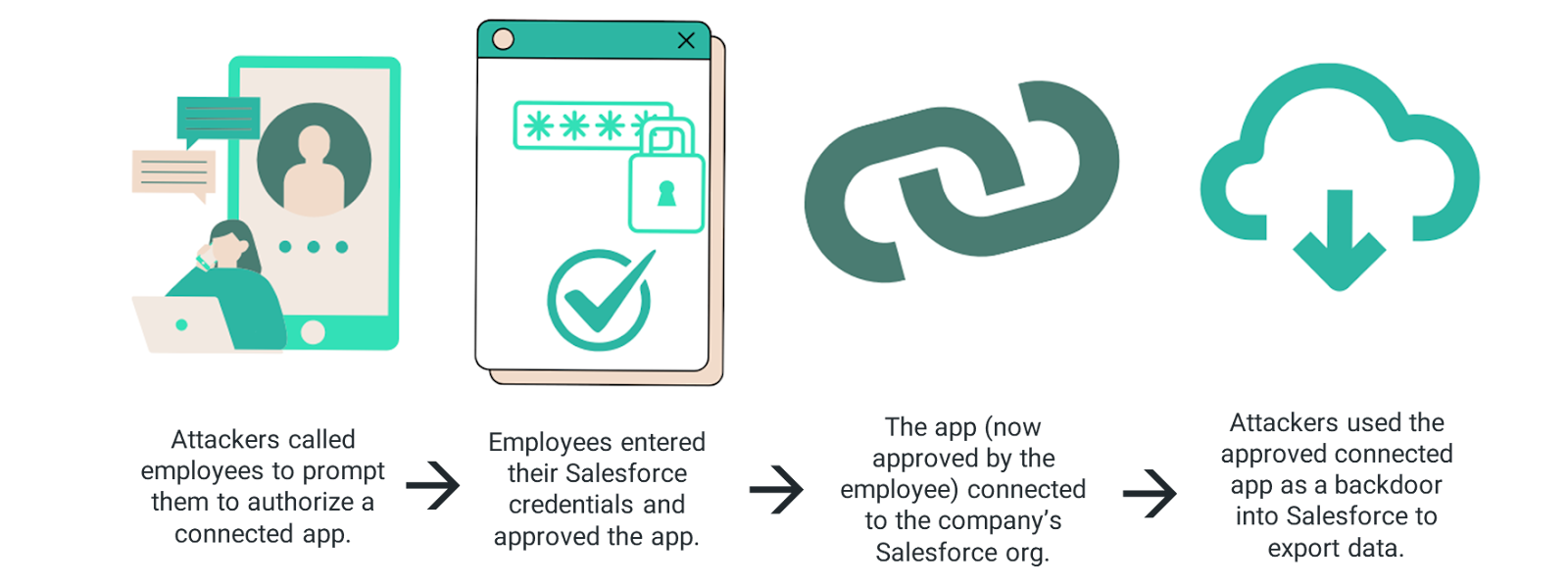
Attackers used a social engineering technique called Vishing (Voice Phishing), that leverages voice calls to trick victims. They called employees at several multi-national organizations and masqueraded as IT support. The attackers prompted employees to install and authorize a fake, hacker-controlled version of Data Loader, a connected app for Salesforce.
Connected apps are applications that users can authorize to gain access to Salesforce. Data Loader is one of many commonly used connected apps, but just like with anything, cybersecurity should always be prioritized and security best practices applied.
Once employees authorized the fake version of Data Loader to access Salesforce, hackers had access to mass export Salesforce data, such as customer accounts.
The vishing attacks have compromised countless organizations, including Google, Adidas, Air France, Chanel, and many others, leading to at least 14 different lawsuits filed against Salesforce.
Salesforce argues that their technology was not compromised and the hackers relied on customers not following security best practices and took advantage of staff having poor cybersecurity training:
“It is important to note that this issue did not stem from a vulnerability within the core Salesforce platform, but rather from a compromise of the app's connection.”
Salesforce offers a suite of security options, but they have to be appropriately configured to be effective. A door lock is only useful if you remember to lock it!
Proactive cybersecurity
Vigilance in cybersecurity isn’t asking whether your organization will be targeted but, rather, asking how your organization will stay safe when it is targeted. Proactive cybersecurity refers to everything you do to anticipate and block a cyberattack from being successful, and it often involves implementing multiple measures.
As technology becomes more advanced, hackers’ attacks can become more sophisticated. This is even more true now as AI-assisted cyberattacks are becoming more common. Cybersecurity can sometimes be tedious, but the time and money lost by being reactive rather than proactive is far greater, not to mention the damage to your organization’s reputation if an incident occurs.
These recent attacks have exposed organizations that didn’t have strong enough layers of security, ultimately putting their stakeholders at risk and leaving them scrambling to defend their reputations.
When there’s a breach, blame is often solely put on the application itself, but the companies owning the data and administering the systems are also responsible for keeping it protected.
How to stay protected
There are many ways to practice better proactive cybersecurity and ensure your organization stays safe so you retain the trust of your stakeholders.
Salesforce customers are responsible for keeping their systems secure by employing proper security protocols and practices. Let’s touch on some of these and why they’re important.
Invest in Training
Your employees have the potential to be your strongest or your weakest layer of protection. System security may start with IT, but it is everyone’s shared responsibility.
It’s critical to make sure your employees understand how to properly identify phishing/vishing and maintain a healthy level of caution when dealing with any third party applications or groups. All it takes is one person making one mistake to jeopardize everything!
Salesforce offers free cybersecurity training on Trailhead, their free online training platform. Their modules are thorough and end-user friendly, if you need a place to start! We recommend Introduction to Cyber Security and Cybersecurity Threats and Threat Actors to begin.
Strengthen Defenses
Training is critical, but training should not be the only measure you take to protect your systems and sensitive data. Human error is a very real possibility.
As we’ve mentioned, Salesforce offers a multitude of security options and implementing these properly helps prevent connected apps from being dangerous backdoors into your org! Let’s touch on each briefly.
- Multi-Factor Authentication
Nowadays, Multi-Factor Authentication (MFA) is a common security practice that you’ve likely experienced before. You may be asked to verify a code sent to your phone in order to access your bank account or click a verification link in an email.
MFA requires a user to have more than one means of verifying who they are. It’s a general cybersecurity best practice, and Salesforce is no exception. It’s recommended to make MFA a requirement to use a connected app.
- Restrict App Access
At your job, you may not be allowed to install new software without IT approving it first. Connected apps should be no different! Lock down connect app access so that only admin-approved connected apps can be used.
If a user wants to connect a new app not on the official list, they have to request it. This lets IT properly vet any new apps before they’re connected.
- User Permissions
Every extra system privilege granted to users is another potential risk to your system and your data. We’ve talked before about how too many system administrators is a huge security risk, and connected apps are yet another reason to maintain the Principle of Least Privilege.
Most Salesforce users won’t need to connect to a large number of new third party applications to do their jobs, so this access should be restricted.
- Salesforce Shield
Salesforce also offers additional products to take your security to the next level! Salesforce Shield is a suite of security tools that extend the standard set of security functionality on the platform.
We can help assess if Shield is a good option for your security needs and, if so, do the implementation for you!
Audit and act, with a free Health Check!
Auditing all of your connected apps and reviewing all of the possible security settings can be overwhelming, but you don’t have to do it alone! We offer Free 24-hour Salesforce Health Checks, which include a review of potential security risks like connected apps and more! In our Health Checks, we can provide you with intelligent connected app insights, including:
- A comprehensive overview of what apps are connected to your Salesforce
- A detailed security audit of any dangerous security gaps in these connected apps settings
- Detailed usage patterns of all connected apps to help identify which of them are active and in use and which can be considered for uninstallation
If you’d like to learn about our recommended method for auditing apps, we put together a mini step-by-step guide that you can follow!
In addition to these invaluable insights, we offer advice on how to proceed with cleanup and adjustments to ensure your connected apps are air tight! Schedule a health check to keep your org safe today! →

.png)

.jpeg)